👾 Overview
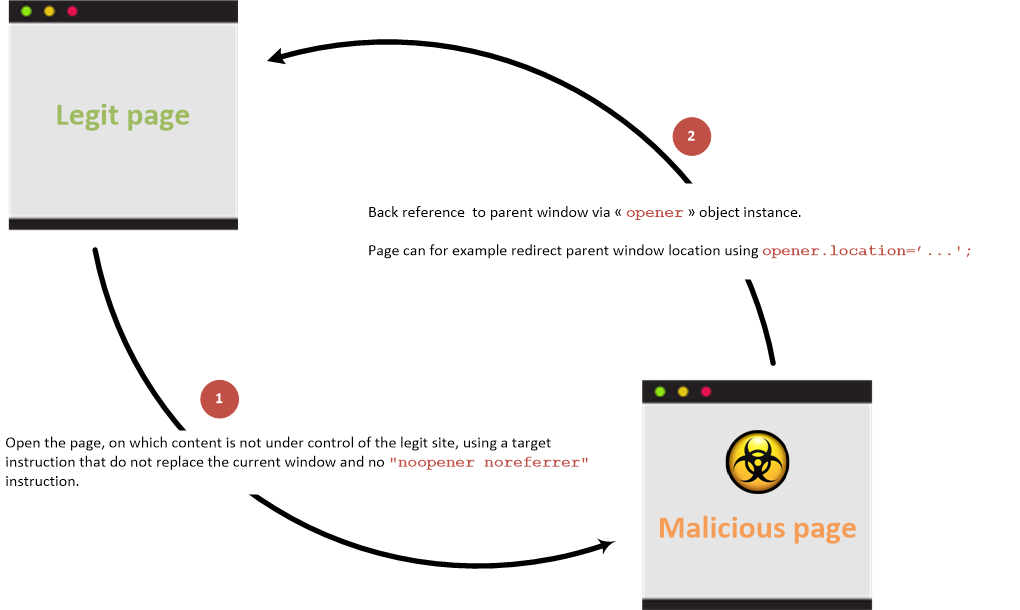
Links which have target="_blank", that do not have rel="noopener" rel="noreferrer" set are vulnerable to reverse tabnabbing.
These links open in a new tab, but the linked page is able to edit the parent page via the opener object. An attacker can spin up a malicious site that redirects users to a phishing site in their original tab.
this only affects legacy browsers, chrome implemented an implicit
rel="noopener"for links withtarget="_blank"in 2021
🔍 Discovery
Look for anywhere users are able to supply links that don’t have rel="noopener" and rel="noreferrer".
Alternatively, you can see if noopener and noreferrer are appended on the client side when supplying a link. If that’s the case you can remove them by intercepting the request with burp.
The burp extension Discover Reverse Tabnabbing will look for this automatically.
📌 Exploitation
To exploit this vulnerability you’ll need to spin up a malicious website which edits the window.opener object to redirect the initial tab.
<!DOCTYPE html>
<html>
<body>
<script>
window.opener.location = "http://super-malicious-phishing-site.com";
</script>
</body>
</html>Generally this would be used to redirect to a phishing site for whatever app you were able to target.
🚔 Prevention
- Don’t allow users to control arguments for links
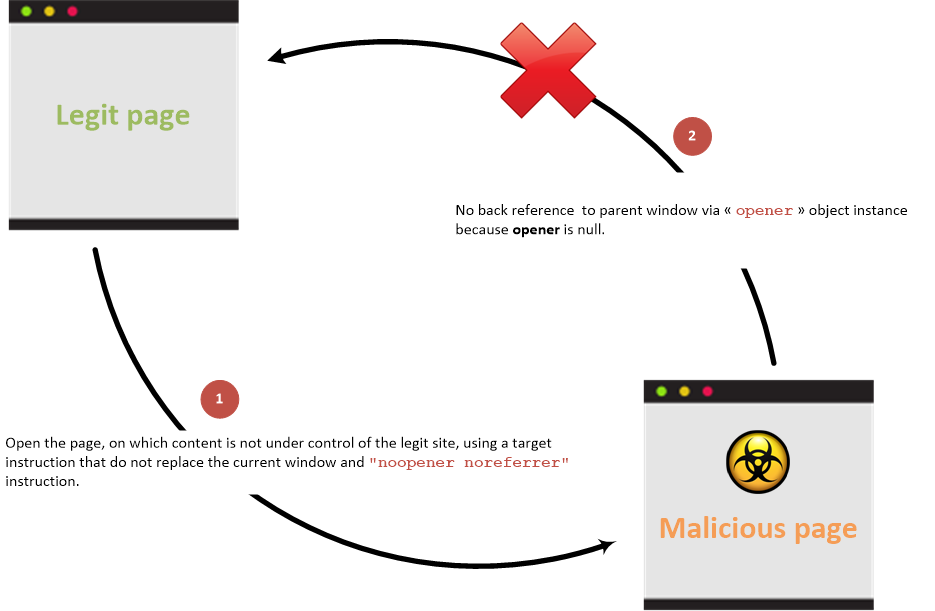
- Append
noopenerandnoreferrerserver side instead of on the client - Use newer browsers which add an implicit
noopenerattribute
📝 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| Chrome Developers | Google’s guidance on noopener and noreferrer |
| OWASP | OWASP Reverse Tabnabbing explanation |
| BApp Store | Burp extension for finding reverse tabnabbing |